Resolve SSL certificate error with Git » History » Revision 37
« Previous |
Revision 37/54
(diff)
| Next »
Redmine Admin, 08/06/2014 09:36 PM
SSL certificate handling with GIT¶
GIT uses cURL internally for transfering files. Unfortunately cURL uses its own certificate-store
and the certificate-chain (Telekom-CA-->DFN-CA-->TU-Clausthal) isn't included by default.
Now, when you try to access a GIT-repository you will get an error similar to this:
Windows
git clone https://scm.in.tu-clausthal.de/git/testgit Cloning into 'stuko1'... fatal: unable to access 'https://scm.in.tu-clausthal.de/git/testgit/': SSL certificate problem: unable to get local issuer certificate
Linux
git clone https://scm.in.tu-clausthal.de/git/testgit Cloning into 'testgit'... error: server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none while accessing https://scm.in.tu-clausthal.de/git/testgit/info/refsThis is because by default cURL does not know the used certificate chain and rejects the GIT operation, which is a good thing to do so.
The solution is to tell Git/cURL about this chain.
- the good and secure method which requires to install the certificate chain used here.
- the bad and insecure method which is based on the fact that GIT/cURL bypasses the SSL certificate verification. The bad and insecure method allows a man-in-the-middle-attack and really should NOT be used. You have been warned! Don't even think about using it. If you are really, really, really ... sure about what you going to to, follow the bad and insecure method.
The good and secure method to use GIT over HTTPS¶
GIT uses cURL for transfering files. Unfortunately the root certificate of the certificate chain used here at the Clausthal University of Technologoy is not included in the default cURL installation. (See this page for further information about TU Claustha-CA)
The certificate chain looks like this:
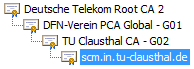
"Deutsche Telekom Root CA 2"
+--"DFV-Verein PCA Global -G01"
+--"TU Clausthal CA - G02"@
+--"scm.in.tu-clausthal.de"
In order to securely work with GIT you need to import the certificate chain.
We will provide the step-by-step-manual for most operating systems.
- Download the certificate-chain from the DFN (Deutsches Forschungs Netz)
Right-click on "Zertifikatkette anzeigen" and select "Save target on"
https://pki.pca.dfn.de/tu-clausthal-ca/pub/cacert/chain.txt - Locate the folder where the git executable is installed.
- On Windows this file is called
curl-ca-bundle.crtand its located most likely atc:\Programs (x86)\Git\bin - On Debian-Linux it is is located at
/etc/ssl/certs/ca-certificates.crt
- On Windows this file is called
- Decide if the certificate-chain should be installed system-wide or just user- or account-wide.
- For a system-wide installation just append the certificate-chain from above to this file-
- On Windows open a administrator console. (Windows-Key->Type "cmd"->right-click on it and select "Run as Administrator" from the pop-up)
cdto the download location and typetype chain.txt >> "c:\Program Files (x86)\Git\bin\curl-ca-bundle.crt" - On Debian-Linux (as root or sudo)
cdto the doenload location and typeecho chain.txt >> /etc/ssl/certs/ca-certificates.crt
- On Windows open a administrator console. (Windows-Key->Type "cmd"->right-click on it and select "Run as Administrator" from the pop-up)
- For a user-wide installation create a copy of the cURL-certificate-store and append
- For a system-wide installation just append the certificate-chain from above to this file-
For user-wide installation make a copy of the *.crt file above and place it in your
To import the certificate chain for GIT follow these steps:
1. Locate the file
https://pki.pca.dfn.de/tu-clausthal-ca/pub/cacert/chain_sha1.txt
To import the certificate chain for GIT follow these steps:
or choose one of the following options to skip the certificate verification:
- Temporary ignore ssl certificate verification:
env GIT_SSL_NO_VERIFY=true git clone https://scm.in.tu-clausthal.de/git/PROJECTNAME
- Disable ssl verfication for one GIT repository (works after first clone):
git config http.sslVerify false
- Globally disable ssl verification (not recommended!)
git config --global http.sslVerify false
Updated by Redmine Admin over 10 years ago · 37 revisions